The evolution of "Password"
The first computer password was developed in 1961 at the Massachusetts Institute of Technology, for use with the Compatible Time-Sharing System (CTSS), which...
1960s

The first computer password was developed in 1961 at the Massachusetts Institute of Technology, for use with the Compatible Time-Sharing System (CTSS), which gave rise to many of the basic computing functions we use today.These first passwords were simple and easily stored, since sophisticated hacking networks and password-cracking programs did not yet exist.
1970s
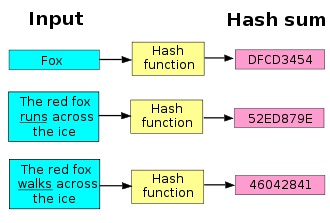
Cryptographer Robert Morris, the father of Robert Tappan Morris, who inadvertently created the infamous Morris worm, developed a one-way encryption function for his UNIX operating system, known as "hashing," which translated a password into a numerical value. The actual password was therefore not stored in the computer system, making the information less readily accessible to hackers.
1980s
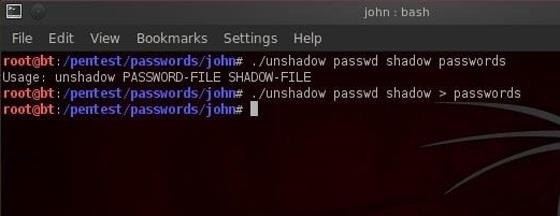
UNIX-based systems such as Linux used a more secure version of the early hashing algorithm which is called "shadow password" file. It's a system file in which encryption user password are stored so that they aren't available to people who try to break into the system. The shadow password file does not entirely solve the problem of attacker access to hashed passwords, as some network authentication schemes operate by transmitting the hashed password over the network , making it vulnerable to interception. Copies of system data, such as system backups written to tape or optical media, can also become a means for illicitly obtaining hashed passwords.
2000s-Today
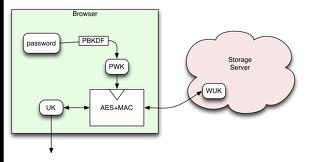
In the last decade, startups and researchers have proposed appropriately futuristic methods to strengthen passwords, or replace them entirely. These range from password management tools like LastPass and 1Password to personal data lockers, which centralize and encrypt passwords and other personal data, to image-based or gesture-based verification systems.
Some companies have already instituted secondary security measures for their employees, for example, by carrying around a small chip that acts as a security key. Similarly, Google recently revealed plans to encrypt data in a small USB key or ring that could act as a password for some devices.